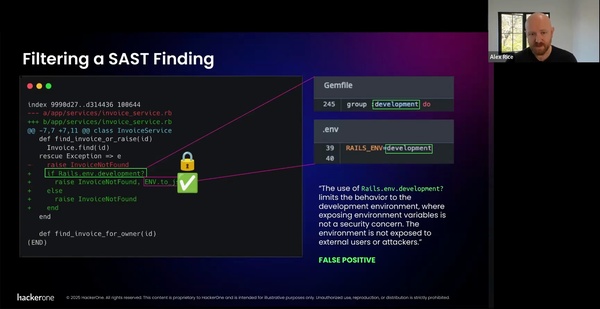
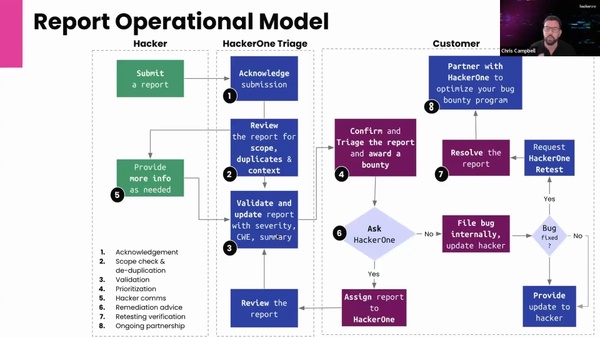
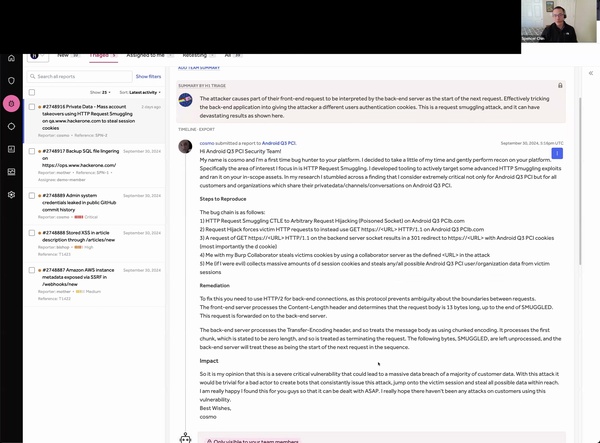
Read More
125 results found
- (11)
- (7)
- (34)
- (26)
- (17)
- (2)
- (4)
- (24)
- (9)
- (12)
- (29)
- (7)
- (17)
- (9)
- (10)
- (7)
- (13)
- (6)
- (4)
- (8)
- (26)
- (35)
- (10)
- (40)
- (9)
- (8)
- (7)
- (5)
- (11)
- (22)
- (1)
- (4)
- (6)
- (3)
- (1)
- (1)
- (2)
- (1)
Video is muted due to browser restrictions. Adjust the volume on the video
player to unmute.
Selected language is not available in captions.

















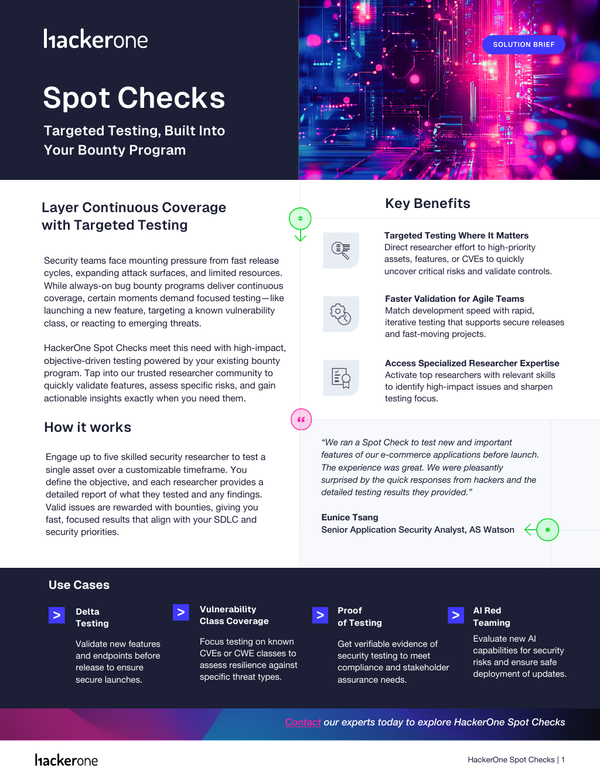





































.png.webp?itok=BL9GYmTI)
.png.webp?itok=318e9Xmj)



-Header.png.webp?itok=86-wtoGI)




.png.webp?itok=9Kajdrft)
_2.png.webp?itok=z33A1bi7)